# Real Time Threat Analysis
Real Time Threat Analysis allows you to monitor hacking activity as it happens on your app. The reports are updated continuously and each hit is reported seconds after it occurs. For example, you can see how many attempts occurred on your application right now, which tools or devices they're interacting with, and on which location threat traffic is more. With Real-Time, you can immediately and continuously monitor active devices, the threats, devices ID's on which hacking attemts are made.
To view ADC Real Time Threat Analysis (console) :
- Open the ADC console at https://console.appsealing.com (opens new window)
- Login with appsealing account credentials
- In the navigation pane, choose 'Real Time Threat Analysis'
Contents
# Metrics
Real Time Threat Analysis shows real-time information about the Application secured with AppSealing. It provides you with the option to set filters on the metrics where you can opt for Operating System (default selected as Android). Data is auto populated periodically based on frequency selected under Refresh Rate.

| Metric | Description |
|---|---|
| Operating System | OS Platform for which the application is sealed Android - Platform used to seal the Native or Hybrid Android apps using Console or CLI tool iOS - Platform used to seal the Native or Hybrid iOS apps using SDK tool |
| Application | Application for which metrics need to be shown, this list will be populated depending on Operating System selection |
| Refresh Rate | Interval(in mins) after data is auto populated |
# Monitoring
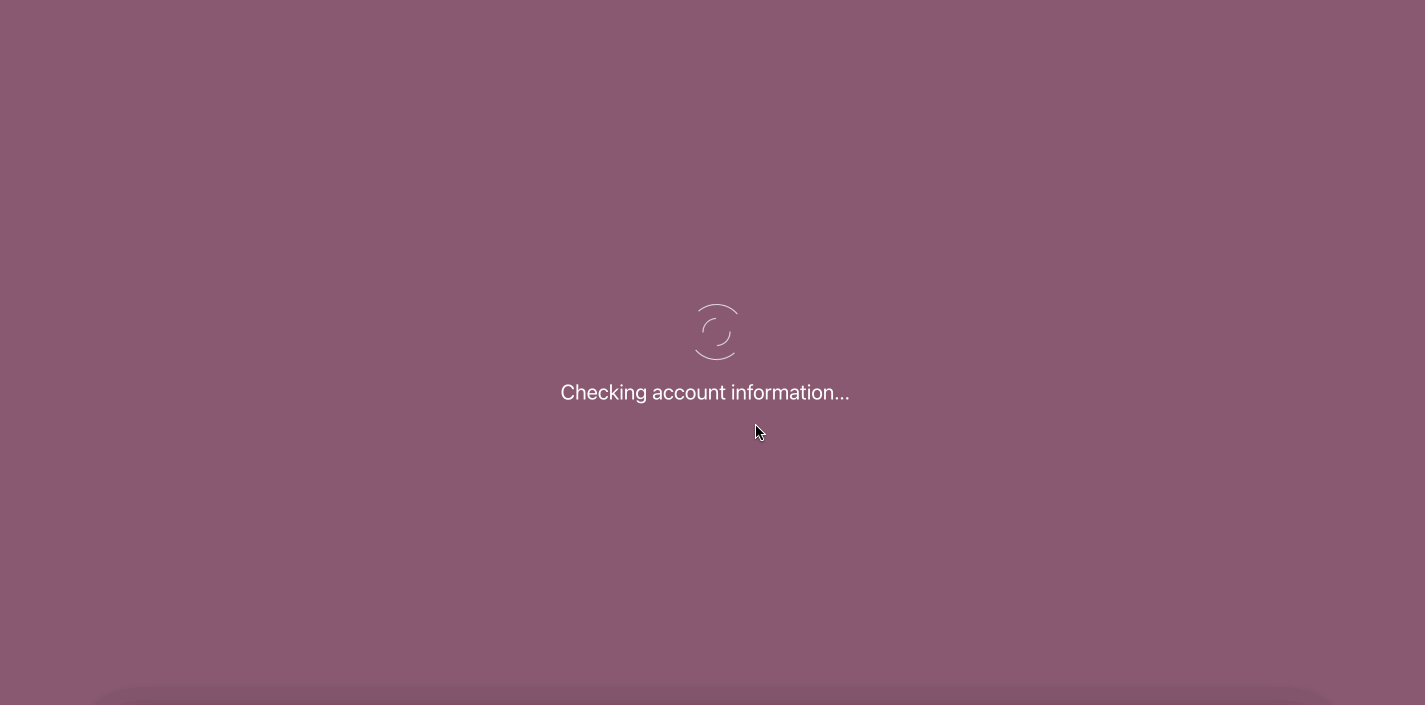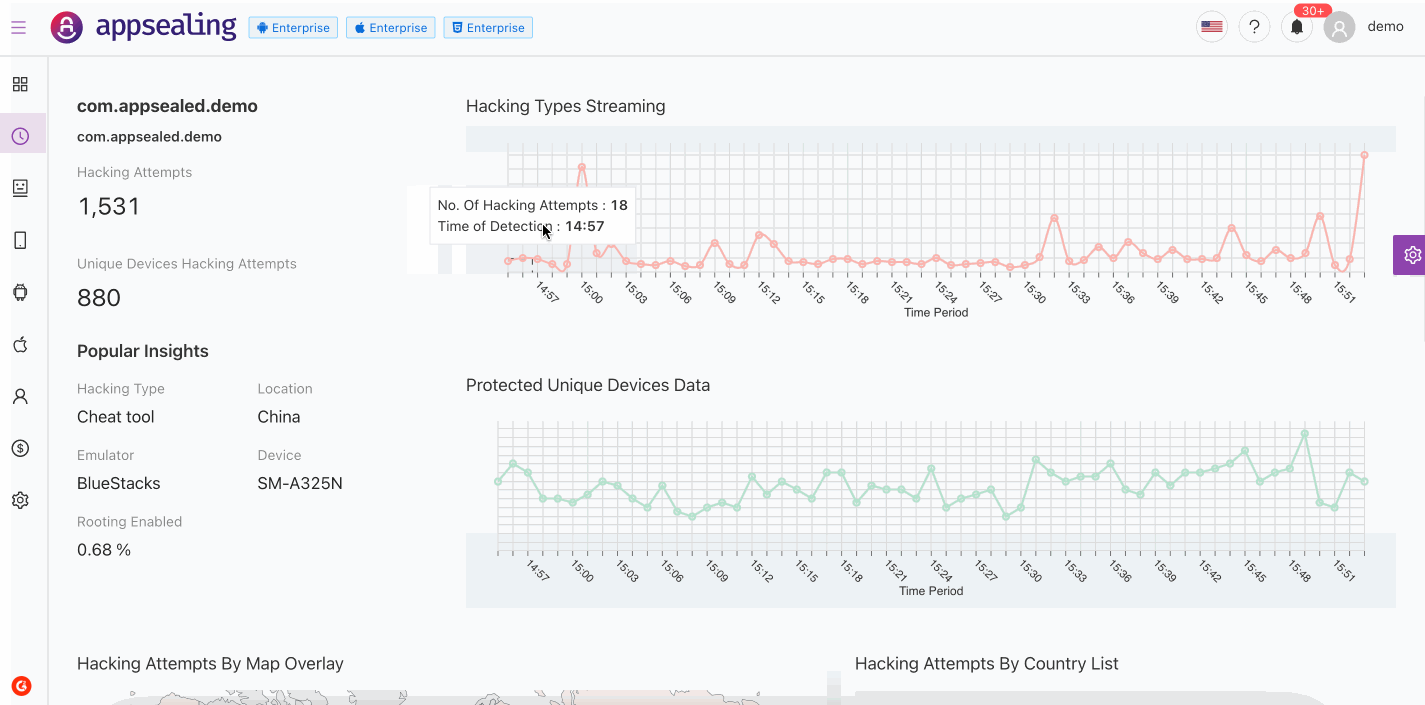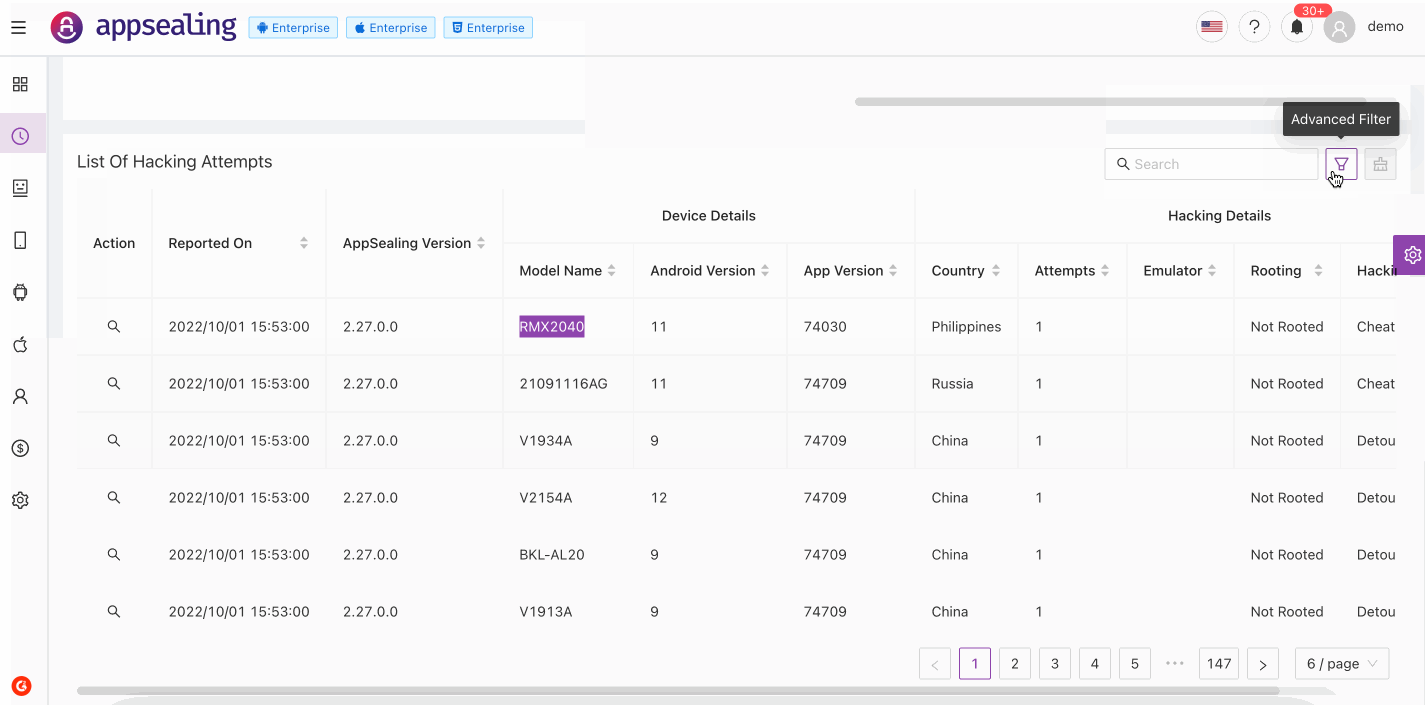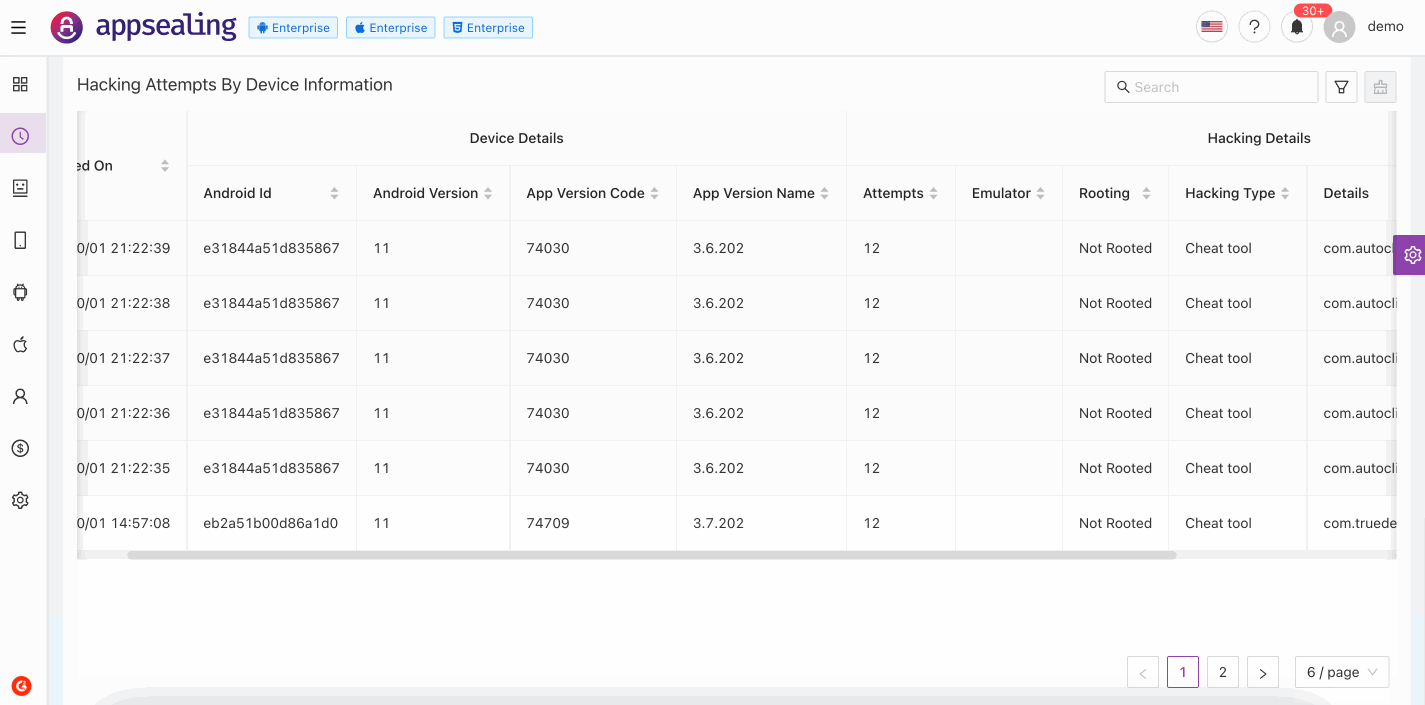
Dashboard monitoring contains overall analytical insights for application, that includes Threat Analytics, Real Time Streaming, Geographical distributions, Hacking Types and many more. Information is shown in tiles and each tile provides needful security information
# Popular Insight
Threat analysis is our in-product threat intelligence solution from expert AppSealing security researchers. It is designed to assist security teams to be efficient for managing emerging threats. Here are a few of the ways you might use Popular Insights:
- monitor Hacking Attempts and Unique Devices Hacking Attempts on your application in last 60mins
- understand which is most common Hacking Type used while attacking devices
- see which country is driving traffic threats to your app
- monitor the immediate effects on traffic from a blog/social network post or tweet
- find out which emulator is commonly used through which app is running
- Device Model from which majority threats are detected
- monitor percentage of rooted devices
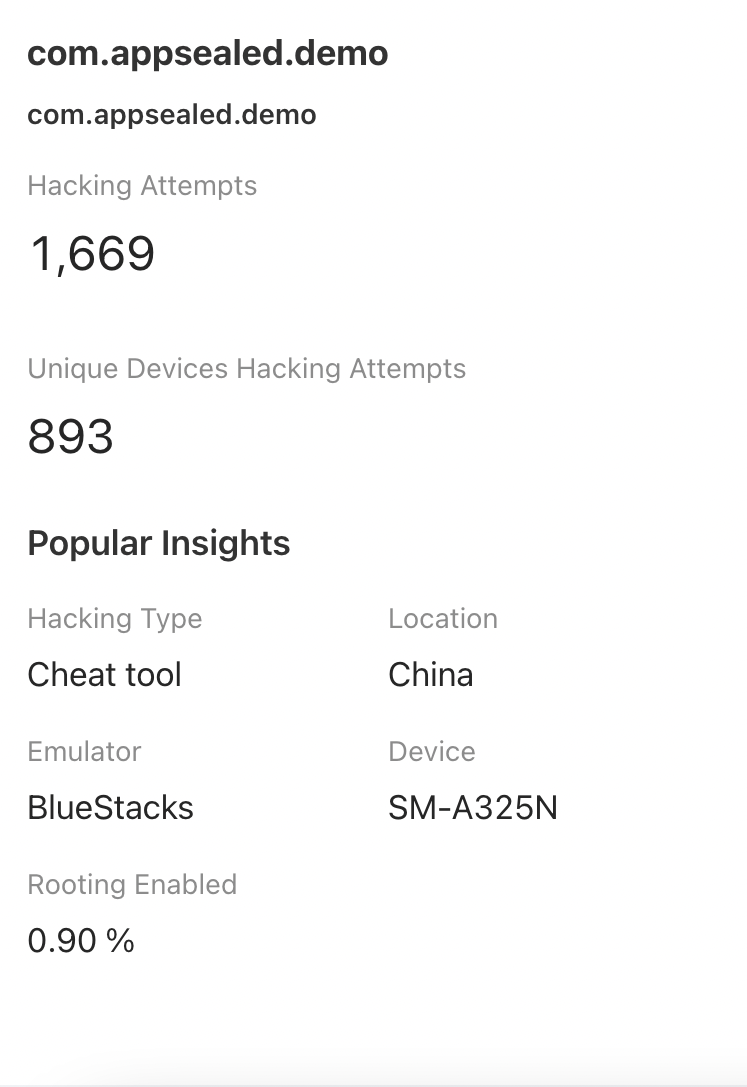
# Hacking Types Streaming
Unique Devices Hacking Attempts shows the number of total hacking attempts per minute occurred in last 60 mins along with top cheat tools and top device models compromised for security
| Axis | Description |
|---|---|
| X-Axis | Date for the selected time period as well as previous month period |
| Y-Axis | Represents number of hacking attempts for selected application |
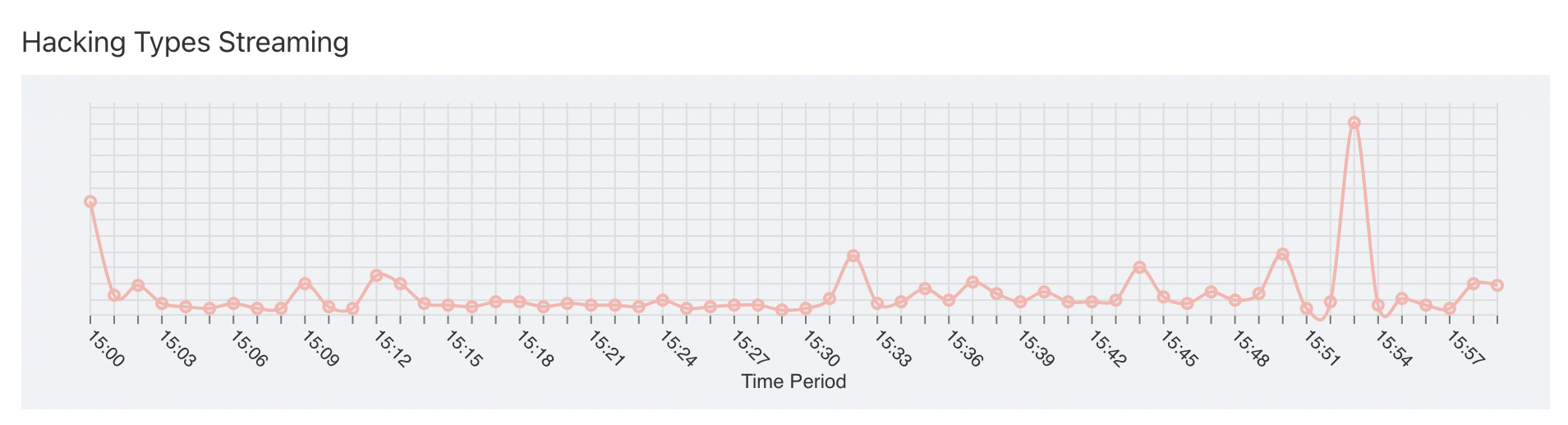
# Protected Unique Devices Data
Protected Unique Devices Data shows the number of total hacking attempts for unique devices per minute occurred in last 10 mins along with top cheat tools and top device models compromised for security
| Axis | Description |
|---|---|
| X-Axis | Date for the selected time period as well as previous month period |
| Y-Axis | Represents number of hacking attempts for selected application |
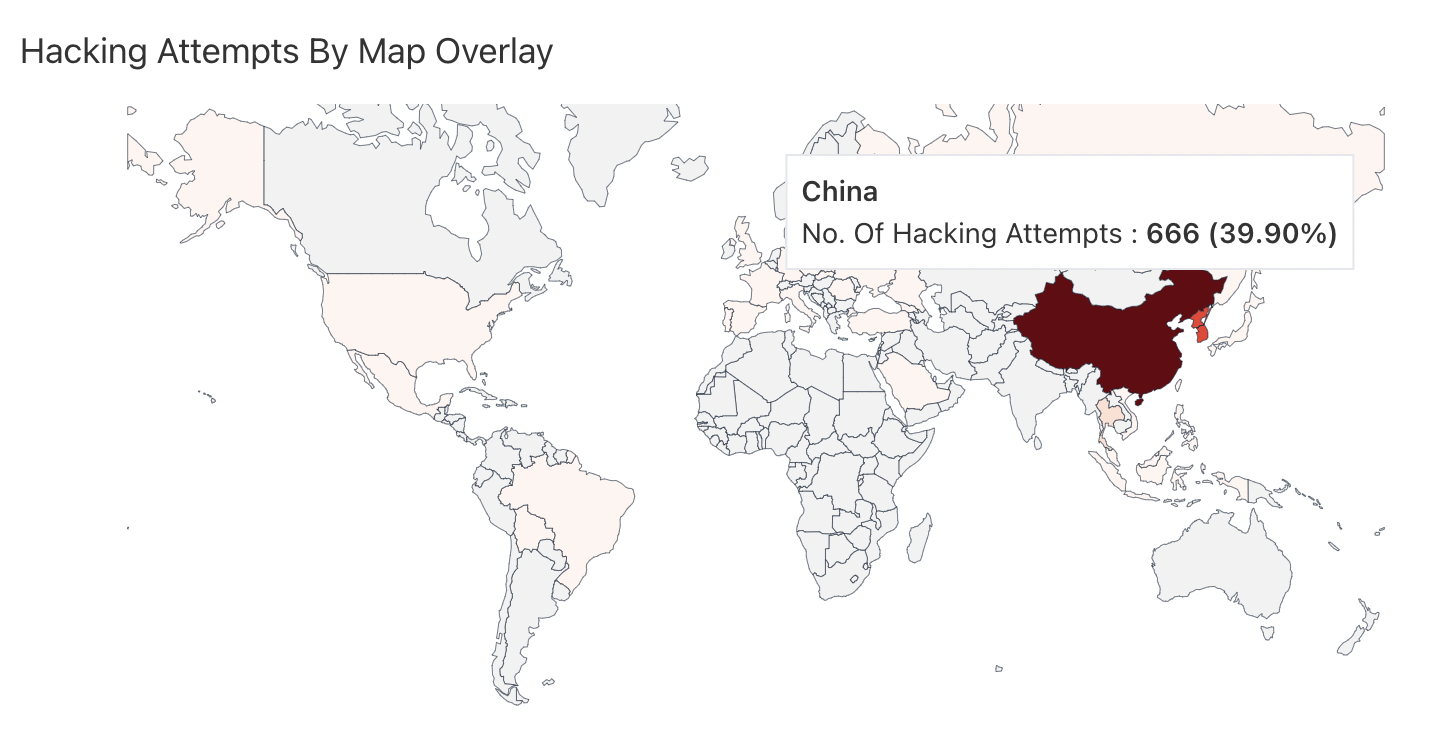
# Hacking Attempts By Map Overlay
Hacking Detections By Map Overlay allows you to view the real time geographic representation of hacking attempted on your application with their hacking information overlaid for last 60 mins. It shows where hacking attempts are coming from with Map overview. Countries are highlighted from light to dark shade based on the number of attempts, higher the number darker shade for the country.
On hover over the countries in map you will find number of Hacking Attempts for last 60 mins.
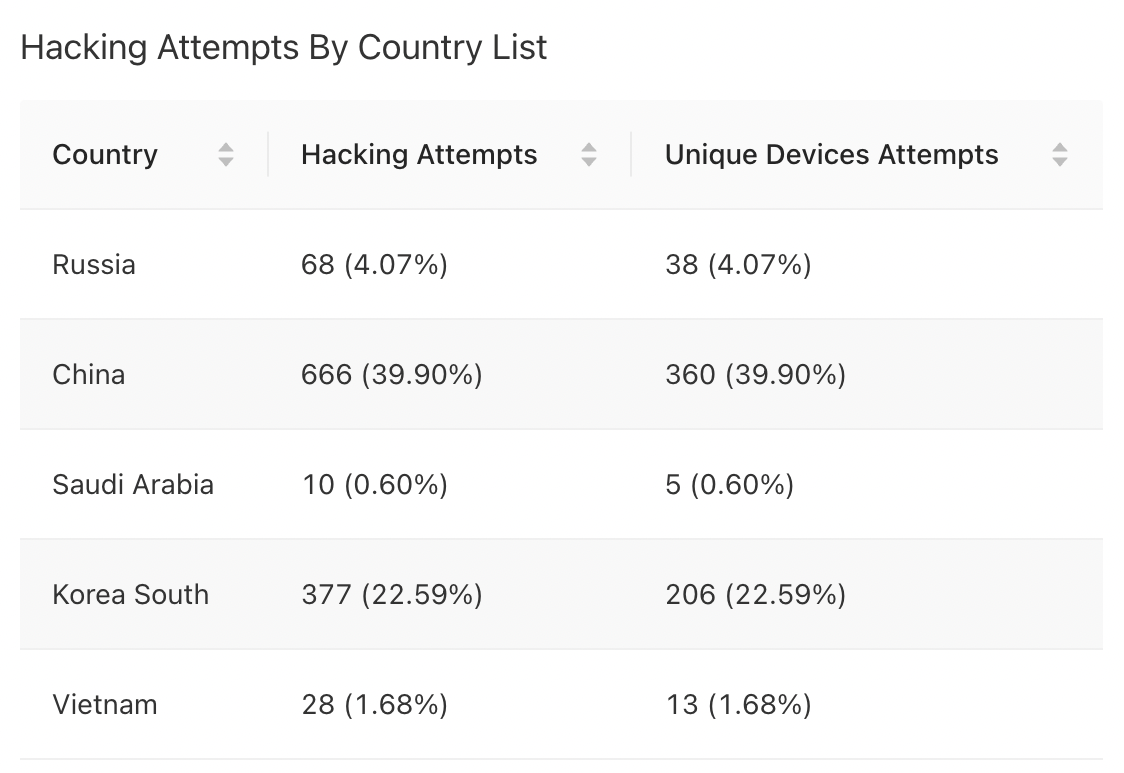
# Hacking Attempts By Country List
This matrix represents hacking information such as hacking attempts and unique device attempts corresponding with the Country. Data displayed for the Top Countries on basis of number of hacking attempts tried on the device
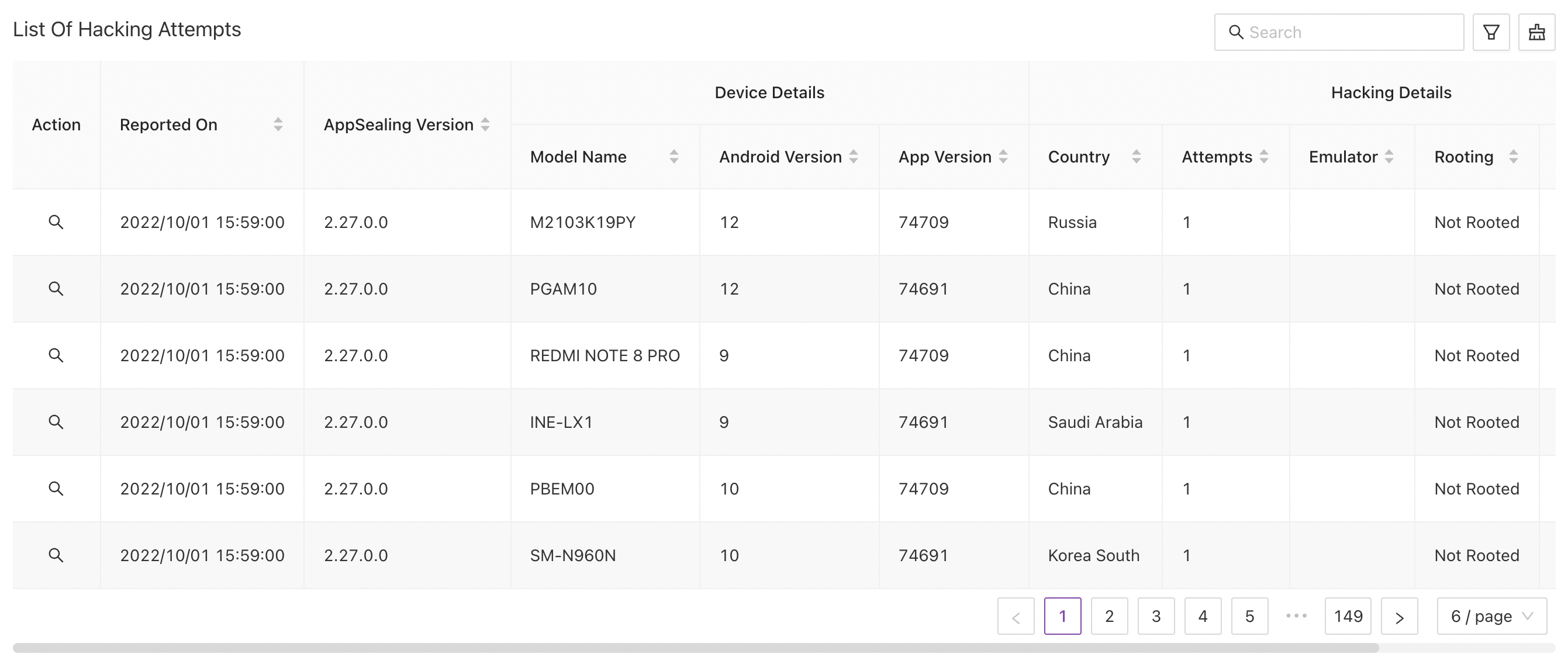
# List Of Hacking Attempts
This table represents detailed hacking information from which threats are reported. You can drill down the result set by specifying filters using search bar or using advanced filters. Records are selectable in the table which will display detailed device information for non-trail users. This result set is populated run-time for last 60 mins and contains useful information such as following:
- Time on which threats are reported
- AppSealing version for sealed app
- Device Details on which hacking attempts are made
- Device Model Name
- Android version for the device
- Application version for your application
- Country from where attempts are made
- Hacking Details
- Number of Hacking Attempts
- Emulator on which app is running (only for android apps)
- Rooting / Jailbreak status for application
- Hacking Type
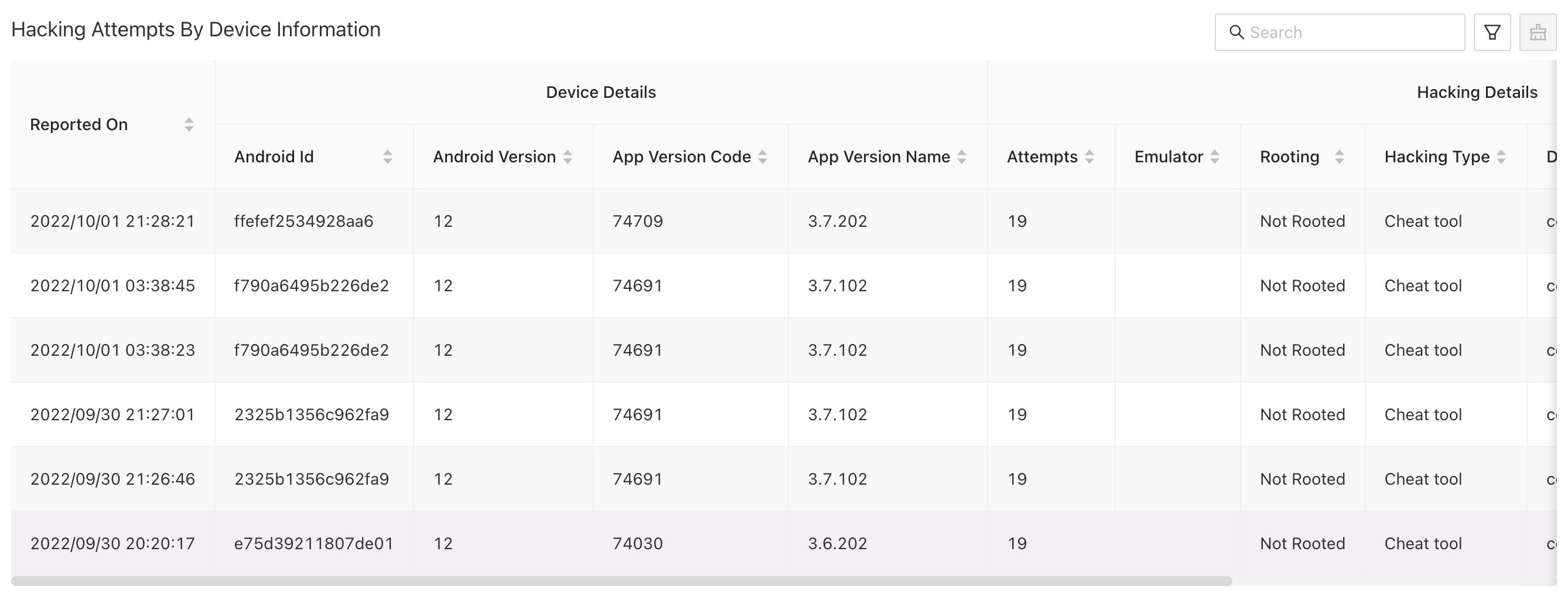
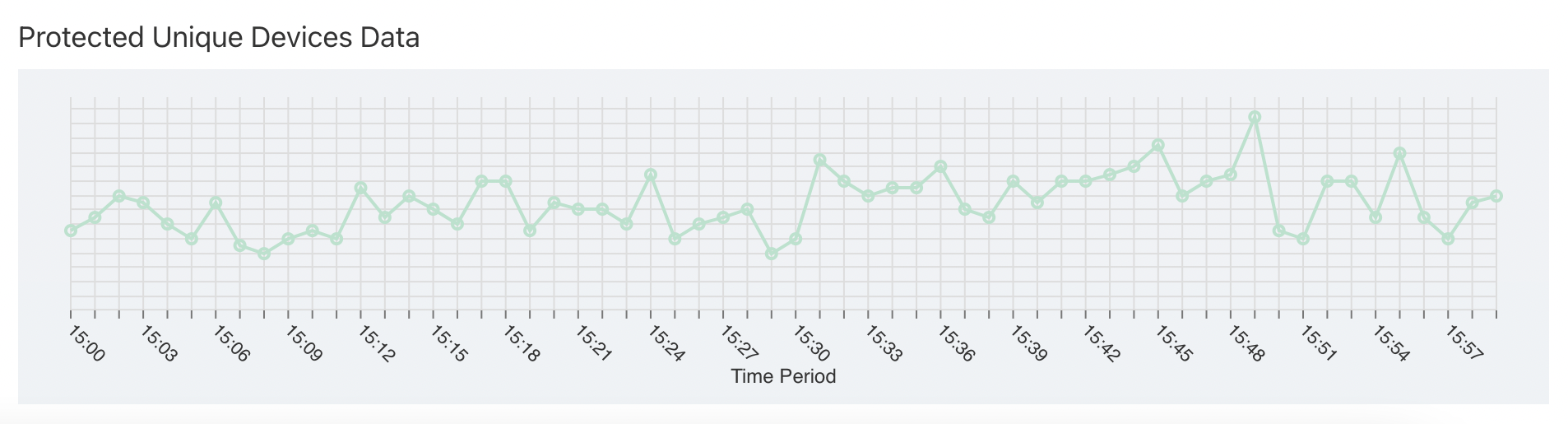
# Hacking Attempts By Device Information
Device Information is available only for professional or enterprise plan customers. This table represents detailed device information from which threats are reported. You can drill down the result set by specifying filters using search bar or using advanced filters. This result set contains useful information such as following:
- Time on which threats are reported
- Device Details on which hacking attempts are made
- Android ID / UUID of user's device
- Operating System version for the device
- Hacking Details
- Number of Hacking Attempts
- Emulator on which app is running (only for android apps)
- Rooting / Jailbreak status for application
- Hacking Type
- Detailed threat information